Yet another day night that curiosity and free time lead me to open burp and start lurking around. This time I will talk about my findings in another of those apps that makes commuting easier which name I agreed not to disclose.
It did not take long to find an interesting JSON response containing (among other things):
“client”:{
“email”:”XXXXXXXXX”,
“firstName”:”Martin”,
“lastName”:”Vigo”,
“id”:XXXXXXXX,
“isAdmin”:false,
“mobile”:”XXXXXXXXX”,
“mobileDigits”:”XXXXXXXXX”,
“mobileCountryCode”:”+1″,
“mobileCountryId”:1,
“mobileCountryIso2″:”US”,
“hasConfirmedMobile”:true,
“hasAmericanMobile”:true,
“hasToOptInSmsNotifications”:true,
“pictureUrl”:”https://XXXXXX.s3.amazonaws.com/XXXXXXX.jpeg”, (masking company name)
“rating”:4.7,
“role”:”client”,
“token”:”XXXXXXXXXXXXXXXXXXXXX”,
“referralCode”:”XXXXX”,
“referralUrl”:”XXXX.com/invite/XXXXX”,
“creditBalances”:[]
}
I removed some of the personal data but as you can see there is some juicy information here. This will focus specifically on the “pictureUrl” and “id” parameters but it is interesting to see that my rating is 4.7 (I am not aware of a way to check your own rating in the app) and some other data I skipped.
The value of the “pictureUrl” key is a url (do’h) that points to the profile picture I uploaded. Is the access restricted? I wish… but no. Anyone can point to that url and see my profile picture.
Now, you may ask, well… but I don’t know the complete url or the format. It is actually not difficult to guess. Someone decided it is a good idea to use the user id as the name for the file. Now, again, you may ask… but I don’t know how the id is formatted. Again, someone decided that starting by 0 and make it incremental (primary key anyone?) was a good idea.
So what?

And what does this all mean? It means that they decided to make publicly accessible all the profile pictures of all their users storing them under predictable urls. You could start by http://XXXXXXXXX.s3.amazonaws.com/1.jpeg and keep going… From what I have seen, they support several image formats so, if .jpeg does not work, try .png. You won’t hit every time a profile picture, my guess is that those are users that did not yet upload a profile picture.
As you can see, there is no breaking into their systems or fancy hacking, you are just accessing publicly available data.
While this might not be the end of the world, it becomes worst when you start to see the kind of stuff that people uploads. Driver licenses with personal data or people that reuses their Tinder profile picture rated-R
Not scared yet? OK, what else can we do… how about if we check the EXIF data of the pictures?
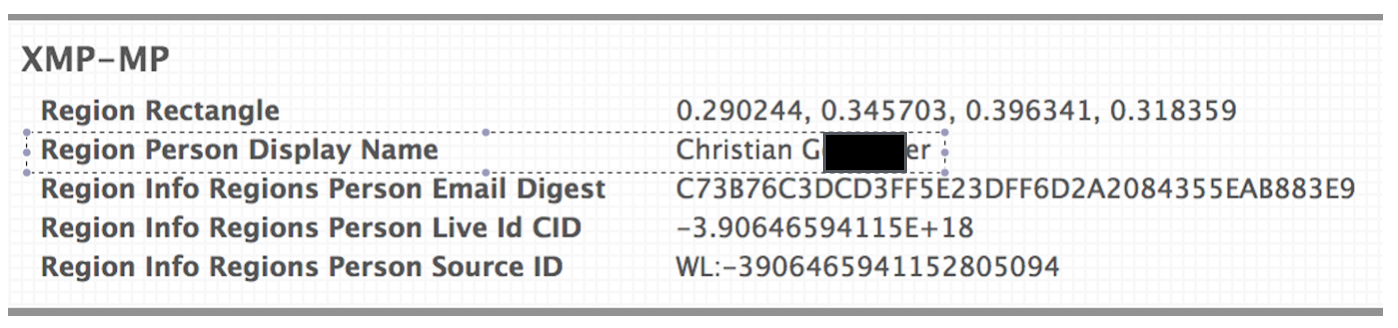
So now we not only have a user id and a picture, we also have a full name.
Is there something else we can find in the metadata? Sure, geolocation of where the picture was taken.
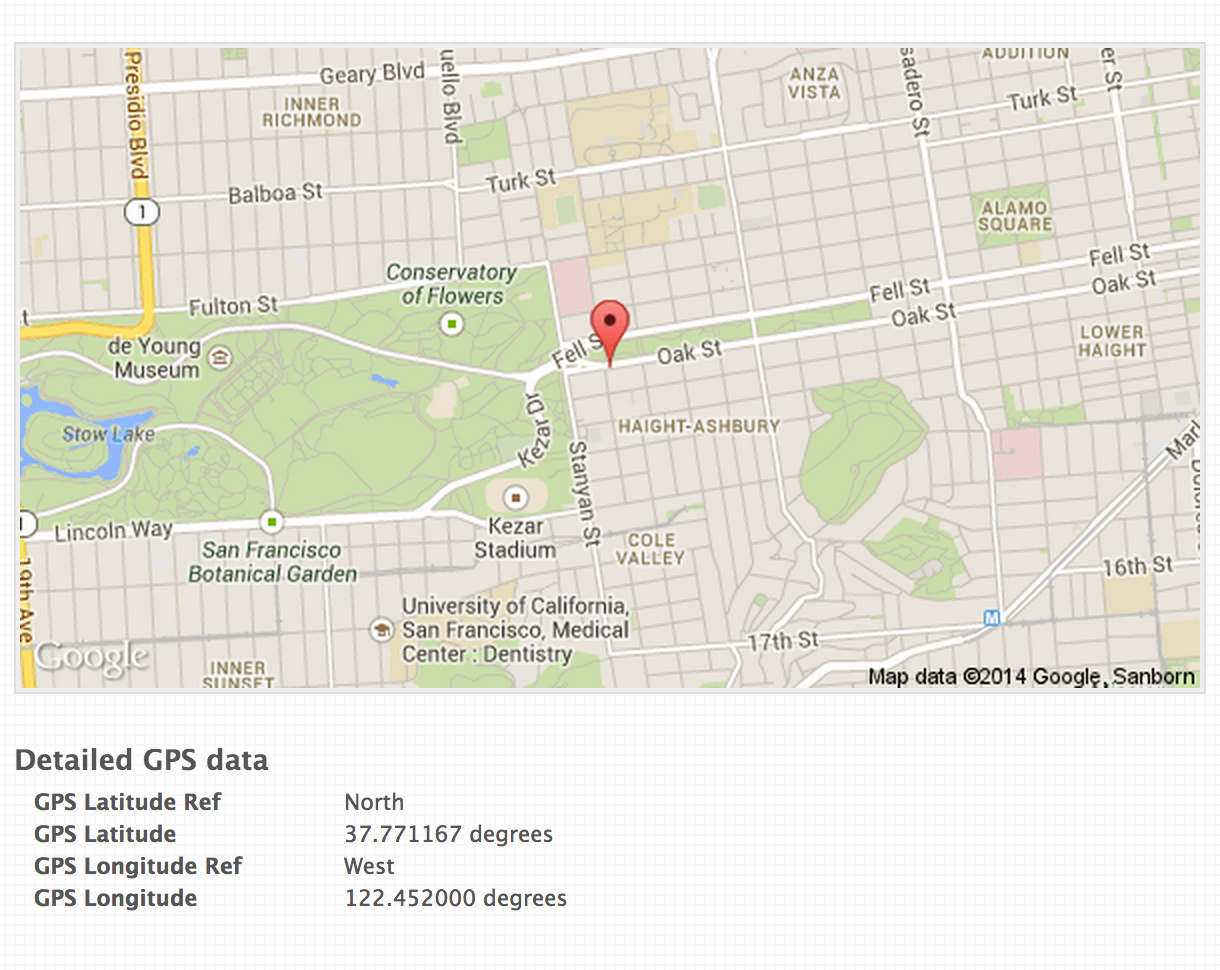
And I know where you live (based on your picture taken in your bedroom).
We could also do a reverse image search and get even more information.
Responsible disclosure
I reported my findings about a month ago to the company and they acknowledged the problem. I suggested the use of UUIDs for filenames and that they remove the metadata. It took them a while to fix it because it takes time to iterate over all the profile pictures to remove metadata and change keys but it is fixed now and we all got a little bit of privacy back. They also added me to their Hall of Fame :D